My final capstone research paper subject I chose pulled me into something big:
Quantum computing isn’t just a new kind of faster computer it changes the rules of trust online. And if we don’t prepare early, the cost won’t just be technical… it’ll be economic and political too.
This article is a simple breakdown of what I learned, why it matters, and what organizations can do right now.
Here is a picture of a quantum computer as of today, in case you don’t know how it looks like.

The research paper is 20 pages long, so here is a summary
- Today’s internet security relies heavily on public-key encryption like RSA and ECC.
- A cryptographically relevant quantum computer (CRQC) could make RSA/ECC unsafe using Shor’s algorithm.
- Attackers don’t need to wait there’s a real strategy called “Harvest now, decrypt later.”
- The biggest risk isn’t the exact year quantum becomes powerful, it’s whether migration finishes before attackers can break it.
- The realistic response is: start now with crypto inventories, crypto agility, and post-quantum migration plans.
Why this topic grabbed me
We don’t usually think about encryption unless something goes wrong. But encryption is like the “invisible plumbing” of modern life:
- online banking
- paying with a card
- logging into a website (TLS)
- software updates
- VPNs
- email security
- even crypto/blockchain transactions
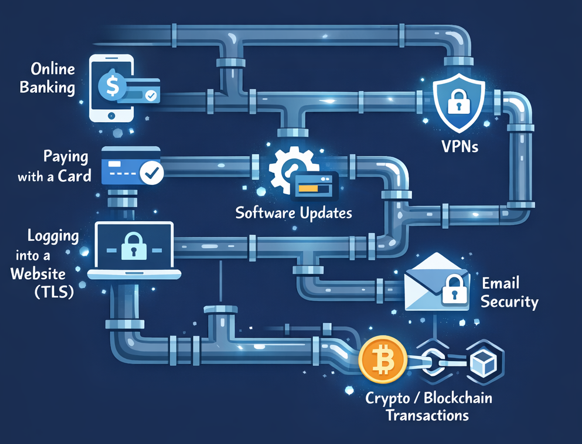
If the trust layer breaks, it doesn’t break in one place, it breaks everywhere.
That’s what made this capstone feel real: it wasn’t just a technical paper. It felt like studying the next big infrastructure shift.
The core idea: quantum changes the security equation
Most of today’s public-key systems work because certain math problems are “too hard” for classical computers:
- factoring large integers (RSA)
- discrete logarithms (ECC)
Quantum computing changes that assumption.
Shor’s algorithm (the big one)
Shor’s algorithm is famous because it can efficiently solve the math RSA and ECC depend on if a sufficiently capable quantum computer exists. click here to go to an article that explains it
That’s why people say quantum can “break encryption.” More precisely:
It can break the foundations of how we authenticate, exchange keys, and sign things digitally.
Here is a picture I found of how it works:
Grover’s algorithm (less dramatic, still important)
Grover’s algorithm speeds up brute-force search. This affects symmetric encryption and hashing, but it’s more manageable because we can compensate by increasing key sizes (for example, moving from 128-bit to 256-bit in many cases). If you need more explanation click here.
So the headline risk is mainly RSA/ECC and the systems built on them.
The scariest part: “Harvest now, decrypt later”
This is the part that made me stop and think. Even before quantum computers can break encryption in real time, attackers can:
- steal encrypted data today
- store it
- decrypt it later when quantum is strong enough
That’s why the timeline matters so much. A simple way to understand it is:
If time-to-break becomes shorter than time-to-migrate, you’re exposed even if you “haven’t been hacked yet.”
This is especially serious for data that stays sensitive for years:
- health records
- government or defense information
- long-term intellectual property
- financial and identity data
Where the U.S. is most exposed
In my paper, one theme kept repeating:
The biggest weaknesses are where RSA/ECC sit inside the “trust stack”:
- key exchange
- digital signatures
- code-signing and update channels
Here’s how that is by sector:
1) Finance + crypto assets
Financial systems rely on trust, authentication, and transaction integrity. If signatures can be forged or key exchange becomes unreliable, it’s not just “a breach” it can cause confidence shocks.
Crypto/blockchains have their own exposure too because many signature schemes (like ECDSA) are vulnerable in a quantum-capable world, and some on-chain public key patterns make targets easier once quantum computing exists.
2) Healthcare
Healthcare is a high-value target because data lives a long time and the privacy stakes are huge. Add real-world constraints like:
- legacy hospital systems
- vendor lock-in
- medical devices that can’t easily update… and migration becomes harder than people think.
3) Federal government + defense
National security depends on secure communications and protected archives. Quantum changes the risk profile because it can expose past encrypted traffic if it was harvested earlier. This isn’t just a technical problem, it’s a trust problem too.
4) Critical infrastructure (energy, water, transport, manufacturing)
Industrial systems often combine:
- older equipment
- long replacement cycles
- safety-first operations
- remote connectivity
That’s a tough environment for a cryptographic transition because upgrades must be planned carefully and tested deeply.
The good news: defending is possible (but adoption is the hard part)
One of the most important lessons I learned is this:
The challenge isn’t only inventing post-quantum cryptography, it’s implementing it at scale.
Post-quantum cryptography (PQC) is maturing, and standards work is already happening. But real migration needs:
1. Crypto inventory (know what you have)
Most organizations don’t have a clean map of:
- where RSA/ECC lives
- which apps rely on them
- which vendors control parts of it
- how certificates are managed
You can’t migrate what you can’t see.
2. Crypto agility (make change possible)
“Crypto agility” means your systems can swap algorithms without rebuilding everything. In practice, it’s the difference between:
- planned migration vs. emergency chaos later
3. Hybrid transitions (practical reality)
Migration often isn’t a “flip the switch.” It looks like running the old classic way and PQC together for a while, testing performance, compatibility, and reliability.
4. Plan for performance constraints
PQC can increase key sizes and computational cost, which matters for:
- IoT devices
- embedded systems
- medical devices
- industrial edge systems
So migration has to be done engineered, not just “approved.”
What surprised me the most
I expected the hardest part to be the math. But the biggest blockers are often human and organizational:
- unclear ownership of crypto components
- fragmented accountability
- budget and procurement cycles
- skills gaps (not enough PQC-ready engineers)
- vendors moving at different speeds
In other words, being ready for the quantum era is a leadership and operations problem as much as it is a cybersecurity problem.
My personal takeaway
The most important line I wrote in my conclusion was basically this:
The decisive variable isn’t the exact year quantum becomes practical, it’s whether migration happens in time.
That’s what I want people to remember.
Quantum isn’t “tomorrow morning,” but it’s also not science fiction. And the biggest mistake would be waiting until there’s a confirmed CRQC timeline and then trying to rush a migration that realistically takes years. At the end of the day, most people don’t have the power to help with migration, so some will get to help or watch the changes from afar.
Writing this capstone made me more excited about cybersecurity and infrastructure than I expected because I got to see other sides of how deeply connected technology, economics, and national security really are.
If you’re curious, I’m happy to share the paper. Leave a comment or send me a message and I would be happy to share.
Question for you: Where do you think the biggest “hidden risk” is right now finance, healthcare, government, or critical infrastructure?
Based on my capstone research paper: “Quantum Computing and Encryption: Economic and Political Implications in the U.S.” (CSIT402, Mount Aloysius College, Nov 23, 2025).